Blog
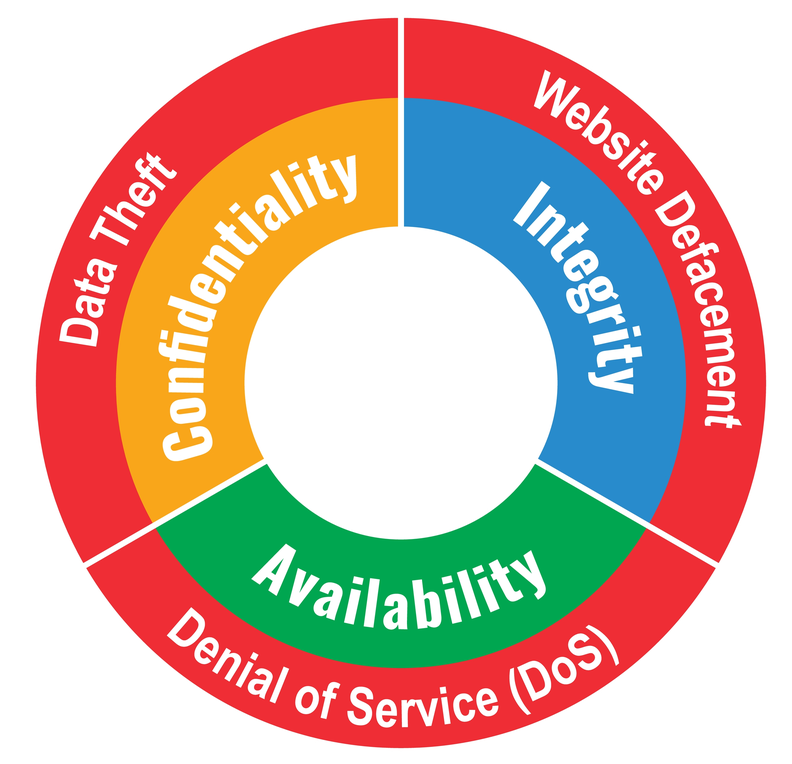
You may have heard of the CIA triad before, but, as is so often the case with such “technojargon”, you may find yourself asking: “What does it really mean to me?” Cybersecurity has three fundamental elements that comprise what is…
Read MoreBad actors are getting smarter and more organized at their craft. Ransomware, Business Email Compromise (BEC), CEO Fraud, spearphishing, vishing… attack vectors are ever-evolving. The solution? Security awareness training and development of a a security-aware culture. Whether you’re just starting…
Read MoreMalicious software—or malware—is used by threat actors to access and infect a computer or network without being detected. Terms like viruses, adware, spyware, ransomware, worms or Trojan horses; these are all different types of malware that can severely damage your…
Read MoreHave you heard the stories about cyber criminals dumping thumb drives loaded with malicious code in employee parking lots waiting for one to be picked up and plugged into a work computer? Pretty clever, right? Unfortunately, studies have found that…
Read More- « Previous
- 1
- 2
- 3