Blog
Does it feel like your IT infrastructure is constantly on fire? Instead of wasting time and resources trying to put out those fires, why not invest in managed IT services? With the right managed IT services solution, you can get…
Read MoreThe digital age has brought about unprecedented levels of connectivity and convenience, but it has also given rise to new threats that were once unimaginable. Cybersecurity has become a pressing issue for individuals, businesses, and governments alike as they try…
Read MoreWhat is malware? Malware is a term used to describe malicious software that is designed to infiltrate your computer and wreak havoc. It can cause serious damage to your system, from stealing personal information to corrupting files or even crashing…
Read MoreA cyber security strategy is a plan of action designed to maximize the security and resiliency of your organization. It uses a top-down approach to establish a set of objectives and protocols to help keep you safe. Why is this…
Read MoreMany business leaders still believe cybersecurity is a problem that can be solved if they invest enough money and hire the right people with the right technical knowledge who will keep them out of the headlines. In fact, it’s often…
Read MoreMore than ever cybersecurity is a business risk, not just an IT problem; yet, many organizations have yet to change their culture of accountability. The CIO or CISO still carry primary responsibility for cybersecurity in 85% of organizations that responded…
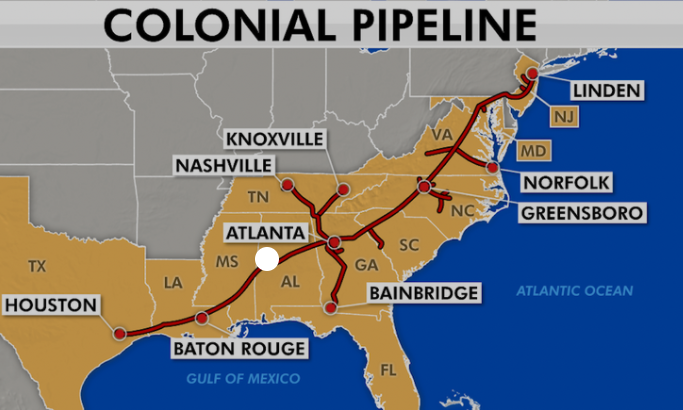
Read MoreCybersecurity attacks on IT infrastructure have become an increasingly legitimate and immediate threat for businesses in the past few years. With the world becoming more technology reliant with each passing day, failure of operations due to a security compromise cause…
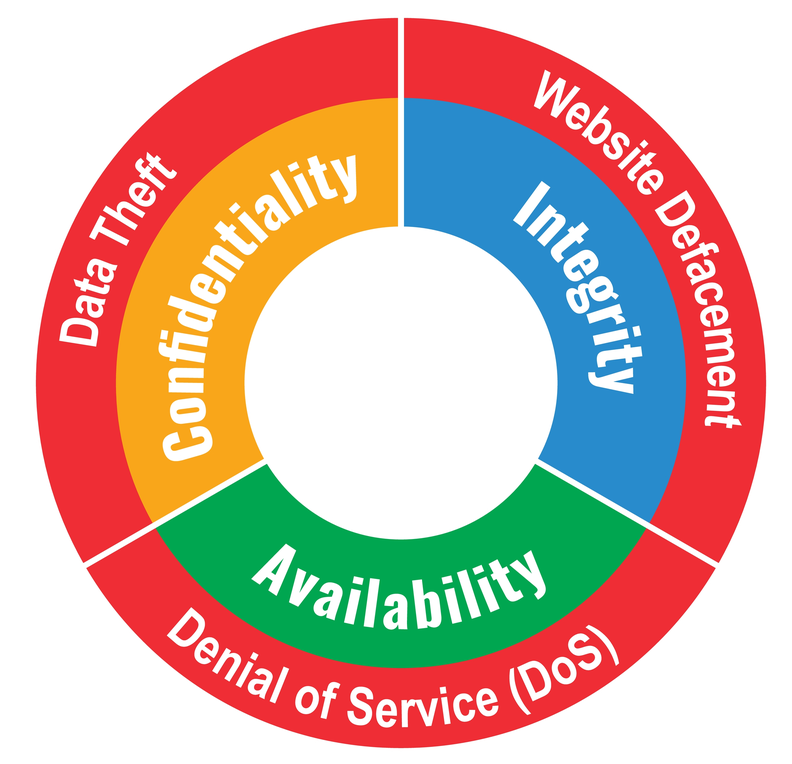
Read MoreYou may have heard of the CIA triad before, but, as is so often the case with such “technojargon”, you may find yourself asking: “What does it really mean to me?” Cybersecurity has three fundamental elements that comprise what is…
Read MoreBad actors are getting smarter and more organized at their craft. Ransomware, Business Email Compromise (BEC), CEO Fraud, spearphishing, vishing… attack vectors are ever-evolving. The solution? Security awareness training and development of a a security-aware culture. Whether you’re just starting…
Read MoreMalicious software—or malware—is used by threat actors to access and infect a computer or network without being detected. Terms like viruses, adware, spyware, ransomware, worms or Trojan horses; these are all different types of malware that can severely damage your…
Read More- « Previous
- 1
- 2
- 3
- 4
- Next »